|
|||
|
1. Introduction to Solaris Trusted Extensions Software 2. Logging In to Trusted Extensions (Tasks) 3. Working in Trusted Extensions (Tasks) 4. Elements of Trusted Extensions (Reference) Visible Features of Trusted Extensions Files and Applications in Trusted Extensions Password Security in the Solaris OS |
Front Panel Security (Trusted CDE)The Front Panel in Solaris Trusted Extensions (CDE) is very similar to the Front Panel that is used in the standard CDE. The Trusted Extensions Front Panel restricts access to only those applications, files, and utilities that you are allowed to use. By clicking mouse button 3 anywhere in the workspace switch area, the Trusted Path menu is displayed. Before you can access a device through the Removable Media Manager, that device must be allocated by using the Device Allocation Manager. The Device Allocation Manager is accessed from the Tools subpanel, which is above the Style Manager icon in the Front Panel. Tip - If you minimize the Front Panel, you can restore the panel by clicking anywhere in the trusted stripe. In Trusted Extensions, Install Icon drop sites are limited to the applications and files that you are permitted to use at the label of the current workspace. For more information about the standard CDE, see the Common Desktop Environment User's Guide. Workspace Switch AreaIn Trusted Extensions, the workspace buttons not only define separate workspaces, but they also require you to work at particular labels. When you begin a multilevel session, each workspace is set to the lowest label that you can use. If your administrator has color-coded the labels at your site, the workspace buttons display the color of the label. The Trusted Path menu is available from the workspace switch area. Trusted Path MenuThe Trusted Path menu contains menu items that affect security, as the following figure shows. Figure 4-4 Trusted Path Menu – Basic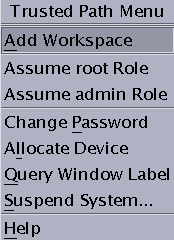 For example, you change your password or allocate devices with this menu. For details, see Performing Trusted Actions. In Trusted CDE, the Trusted Path menu has a second version. The Workspace Name version includes additional workspace options. The selections that appear in your menu depend on how the administrator configured your account. Figure 4-5 Trusted Path Menu – Workspace Name Version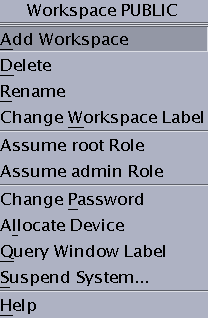
Clock SecurityIn Trusted Extensions, only an administrator can change the date and time that is set for your workstation. Calendar SecurityThe calendar shows the appointments for you at the label of your current workspace only. To view appointments at a different label, you need to open the calendar at that label. File Manager SecurityIn Trusted Extensions, the File Manager displays files at the label of the current workspace. To view files at more than one label at a time, you run the File Manager from workspaces at different labels. You then use the Occupy Workspace command to display the different File Manager windows in the same workspace. The File Manager enables you to change a file or folder's basic permissions and access control list (ACL). If you are authorized, you can also move or link files between File Managers at different labels. For details about File Manager use, see How to View Your Files in a Labeled Workspace and Performing Trusted Actions. Text Editor SecurityA text editor can be used to edit files at the label of the current workspace only. If you are authorized, you can copy information between text editors at different labels. Personal Applications SubpanelThe default applications in the Personal Applications subpanel operate similarly to the standard CDE environment. The Terminal icon opens the default shell that is assigned to you by your administrator. To access a web server, the label of your browser must be the same as the label of the web server. Mailer SecurityIn Trusted Extensions, all mail messages are labeled. When you send a message, it is sent at the label of your mail application. Only hosts and users that are cleared for that label receive the message. Only users who are working at that label can view the message. If you need to use the vacation message option in your mail application, you must explicitly enable vacation message replies for each label at which you typically receive mail. Check with your security administrator for your site's security policy on vacation messages. Printer SecurityThe Print Manager in the Personal Printers subpanel displays icons for all printers that are accredited up to your clearance. However, you can use only those printers that are accredited to print documents at the label of the current workspace. A typical print job in Trusted Extensions includes labels and extra pages, as follows:
A typical banner page appears in the following figure. The words JOB START indicate the banner page. Figure 4-6 Typical Banner Page of a Labeled Print Job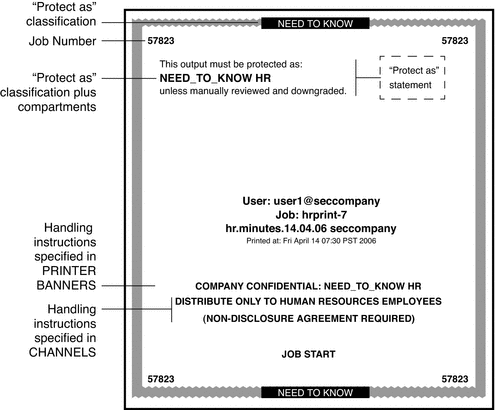 For the exact security information regarding printing at your site, see your administrator. Style Manager SecurityWith three exceptions, the Style Manager operates in the same manner as on a Solaris system.
Application Manager SecurityThe Application Manager provides access to only those applications and utilities that your administrator has assigned to you. In a role, you have access to a different set of applications and capabilities. Remember that the ability of a function to operate on a file depends on the label of the current workspace. Similarly, although you can add applications to the Personal Application subpanel by dropping icons onto the Install Icon drop site, you can only run an application if your administrator has assigned the application to you. Trash Can SecurityIn Trusted Extensions, the trash can stores files to be deleted by label. Although you can drop files at any label in the trash can, the trash can displays files at the current label only. You must delete sensitive information as soon as the information is in the trash can. |
||
|